Federal Cybersecurity Challenges
These days, when you turn on the news you almost always see another hack, leak, or breach putting sensitive information at risk. But we’ve been focusing on keeping federal agency information systems secure for a long time. For October’s Cybersecurity Awareness Month, the WatchBlog takes a look at federal cybersecurity challenges.
What is the threat?
Cybersecurity incidents can pose serious challenges to personal privacy and security as well as the economy and national security.
The breach at the Office of Personnel Management that was first reported in July 2015 is a good example of both. At least 21.5 million individuals had their personal data leaked, leaving them vulnerable to identity theft, fraud, and security threats. As most of the affected individuals were also government employees—many of whom are entrusted with sensitive or classified information—the breach was also a matter of national security.
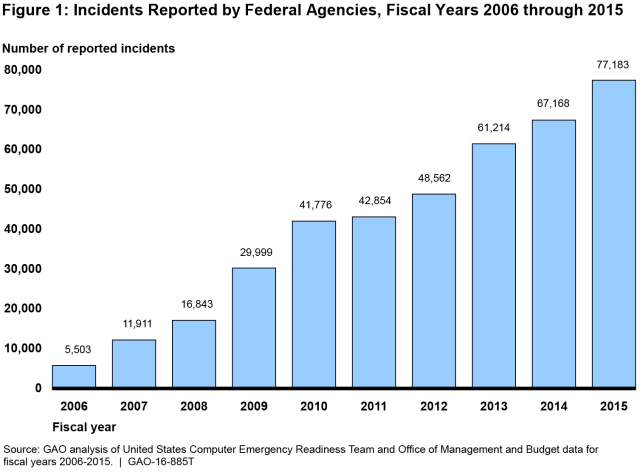
And the number of reported information security incidents at federal agencies is growing—up more than twelvefold from 2006 through 2015.
(Excerpted from GAO-16-885T)
Who’s behind all these incidents?
The threats to federal IT systems and networks come from a variety of sources and vary in terms of the types and capabilities of the actors, their willingness to act, and their motives. Here are some of the likely perpetrators:
- Hackers/hacktivists: people who break into networks for challenge, revenge, stalking, monetary gain, or to further political goals
- Malicious insiders: employees or contractors who can gain access to networks and systems through their positions in the organization
- Nations: nations and states that sponsor or sanction cyber attacks for espionage or information warfare
- Criminals and organized crime: criminal groups who attack systems for monetary gain
- Terrorists: people who use cyber attacks to threaten national security, cause mass casualties, weaken the economy, and damage public confidence.
- Unknown malicious outsiders: unknowns
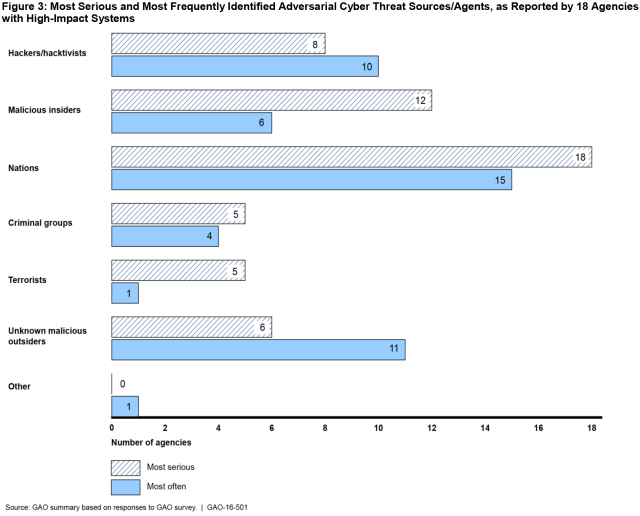
Our survey of federal agencies found that the 18 agencies with “high-impact systems” (i.e., those that hold sensitive information, the loss of which could cause catastrophic harm) identified cyber attacks from nations as the most serious and most frequently-occurring threat.
(Excerpted from GAO-16-501)
Why can’t agencies stop the attacks?
Several laws and policies establish a framework for how the federal government should protect its information systems. However, we reported that agencies are not consistently implementing the framework, and additional actions are needed. For example, agencies should
- patch vulnerable systems and replace unsupported software
- comprehensively test security on a regular basis
- strengthen oversight of IT contractors
- better identify cyber threats
- improve their responses to cyber incidents and data breaches, and
- better recruit and retain a qualified cybersecurity workforce and improve workforce planning activities at agencies.
So why isn’t this happening? The 24 agency Chief Information Security Officers we surveyed frequently cited these hurdles to overseeing information security activities:
- competing priorities between agency operations and information security
- difficulties coordinating with other offices and component organizations
- lack of security-related information from internal offices and IT contractors
- IT contractors and other staff not directly under a chief’s control, and
- the position of the CISO in the agency’s hierarchy.
Over the past several years, we have made about 2,500 recommendations aimed at strengthening agencies’ information security programs and controls. It will take coordinated effort across the government, with strong strategic direction from the White House and effective oversight, to make sure that federal agencies are taking all the necessary steps to protect our nation’s systems and information.
- Comments on GAO’s WatchBlog? Contact blog@gao.gov.
GAO Contacts
Related Products

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to blog@gao.gov.