Cybersecurity—New Risks and Threats
Picture this:
- Atlanta’s municipal information system was hit with a cyberattack that prevented customers from accessing multiple applications, including paying bills and viewing court-related information.
- The Department of Justice reported indicting nine Iranians for a massive cybersecurity theft campaign on behalf of the Islamic Revolutionary Guard Corps. They allegedly stole more than 31 terabytes of documents and data from more than 140 American universities, 30 U.S. companies, 5 federal government agencies, and others.
- A breach at Equifax resulted in the loss of personally identifiable information for an estimated 148 million U.S. consumers. According to Equifax, the hackers accessed people’s names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers.
Seems like a lot of cybercrime, doesn’t it? These were just the headlines from this past year.
Today’s WatchBlog highlights the testimony of U.S. Comptroller General Gene Dodaro on cybersecurity challenges that urgently require federal action.
New Technologies, New Risks
Federal agencies and the nation’s critical infrastructures—energy, transportation, communications, and financial services—depend on increasingly complex information technology systems. This complexity makes it harder to identify, manage, and protect all system and network components.
New attack technologies are changing the threat landscape. For example, government and critical infrastructure systems have always been vulnerable to both insider threats and foreign attackers. However, attackers may be able to do more damage than before as technologies and methods, such as those used to carry out denial-of-service attacks, steadily advance. Threats around the globe are emerging and escalating, with foreign adversaries gaining expertise and being backed by governments and others with significant resources.
Networks are also becoming more vulnerable due to the growing popularity of the Internet of Things—technologies and devices that gather data and communicate it to the Internet or other networks. It has increased the number of devices, networks, and cloud servers that could be compromised in an attack.
Privacy in an Increasingly Connected World
Many of these IT systems contain vast amounts of personally identifiable information such as name, date and place of birth, and other types of personal information that can be linked to an individual, such as medical or educational information.
Powerful search technology and data analytics software have made it easy to correlate information about individuals across large and numerous databases. In addition, ubiquitous Internet connectivity and devices, such as smartphones and fitness trackers, have facilitated sophisticated tracking of individuals and their activities.
Government databases that contain information that could be used to identify individuals must be protected from both inappropriate access (i.e., data breaches) and inappropriate use (i.e., for purposes not originally specified when the information was collected).
The Office of Personnel Management has seen firsthand what can happen when such databases are compromised. In June 2015, OPM reported that an intrusion had affected personnel records of about 4.2 million current and former federal employees. Then, the next month, the agency reported that a separate, but related, incident had compromised files related to background investigations for an estimated 21.5 million individuals.
Rising to the Challenges
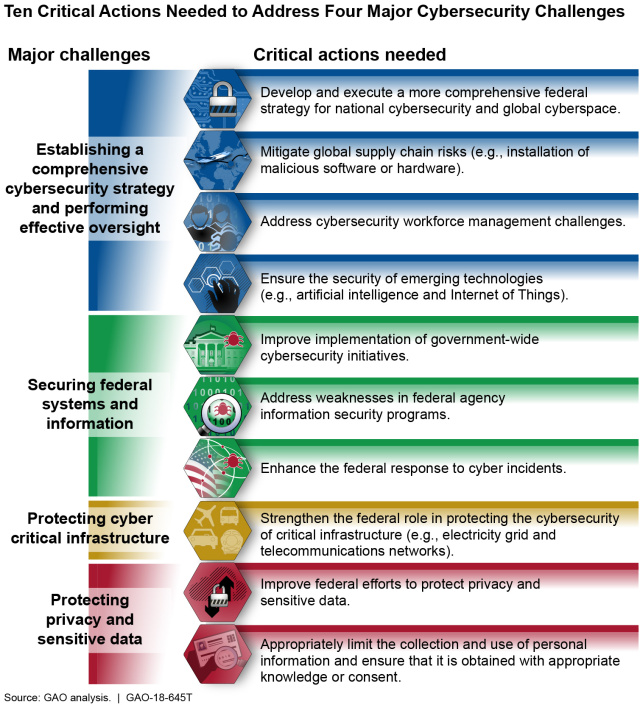
We have identified four major cybersecurity challenges and 10 critical actions that the federal government and other entities need to take to address them:
We have also made over 3,000 recommendations to agencies since 2010 aimed at addressing cybersecurity shortcomings. As of July 2018, about 1,000 had not been implemented.
Check out our testimony to learn more.
GAO Contacts
Related Products

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to blog@gao.gov.