Risky Business—Threats in the IT Supply Chain
Laptops aren’t like IKEA furniture—we usually buy them pre-assembled and ready to use. The life of a computer starts long before it’s purchased, though, and the process of creating and moving a computer from suppliers to users can create security risks.
In today’s WatchBlog, we take apart the IT supply chain process and explore the vulnerabilities in that process.
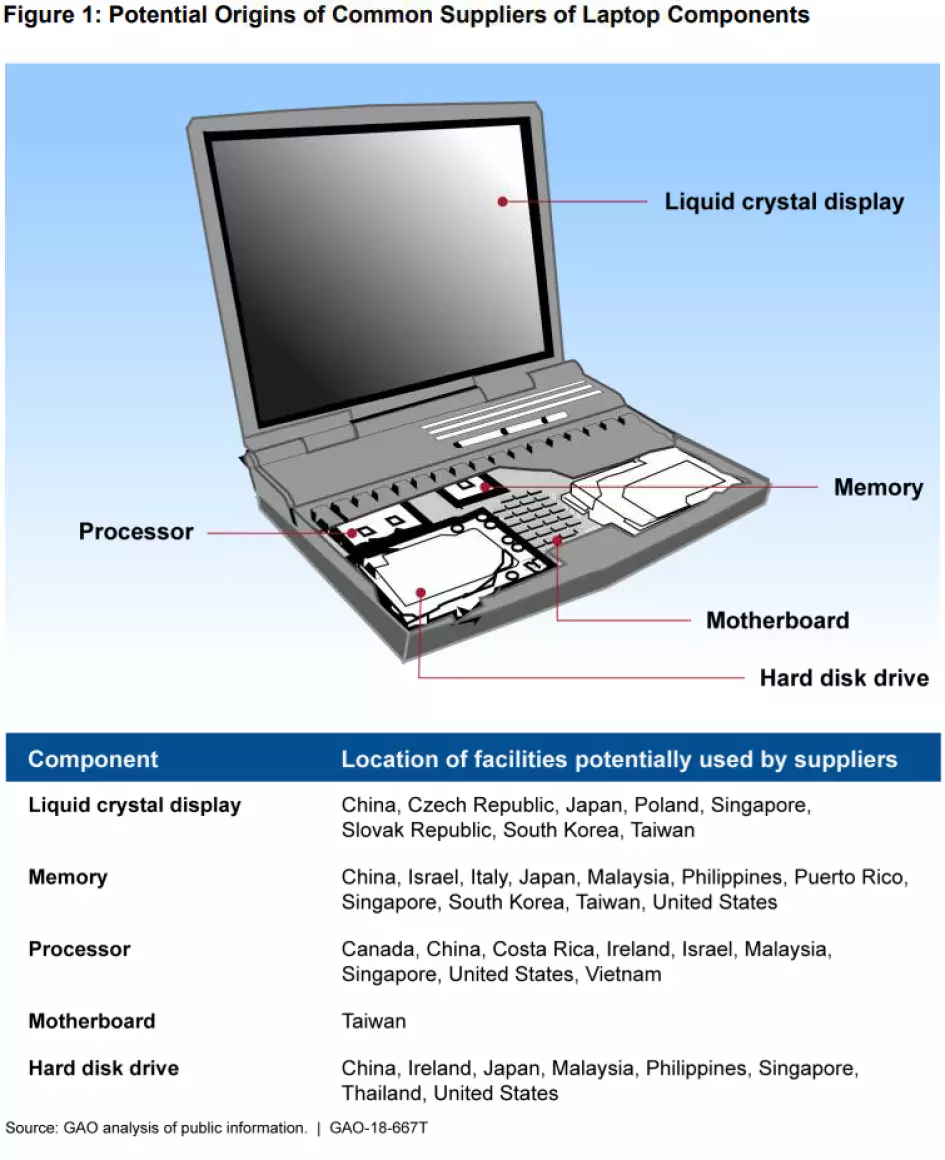
Where do the parts in a laptop come from?
IT system supply chains—including the companies, people, and activities that go into creating computers, software, or services—are long, complex, and global. Even for just one laptop, many of the manufacturing components are acquired from various sources around the world.
Vulnerabilities in the IT supply chain
The complex supply chain process can pose a problem for federal agencies that rely on IT systems to function. Since agencies have little visibility into how the technology they buy was made, they can’t be sure those systems are secure. There are many vulnerable points in the IT supply chain. Unauthorized distributors, inadequate software testing, and untrustworthy suppliers can all introduce risks. Bad actors can take advantage of these vulnerabilities by
- installing intentionally harmful hardware or software.
- installing counterfeit hardware or software, or
- causing a failure or disruption in the production or distribution of products critical to federal agency operations (e.g., due to labor or political disputes
Bad actors don’t need to be a part of the supply chain to pose a threat, either—they can take advantage of unintentional vulnerabilities such as defective code, for instance.
And in some cases, agencies may unwittingly introduce risks by relying on malicious or unqualified contractors or service providers to perform technical services, giving them access to sensitive information.
Are federal agencies addressing computer threats?
The 4 agencies we reviewed in 2012—the Departments of Defense, Justice, Energy, and Homeland Security—varied in their responses to IT supply chain threats.
At the time, DOD had made the most progress in managing the risks that computer suppliers, hackers, counterfeit goods sellers, and others presented. It had set up policies to protect its chain of suppliers and to check on whether the policies were effective.
We recommended 8 actions that Justice, Energy, and Homeland Security could take to better manage possible risks in their chain of suppliers, including
- developing and publishing methods to improve department security, and
- setting up a way to judge whether these actions are effective.
By 2016, the agencies had installed methods to carry out 7 of the recommendations and had partially carried out the 8th. By implementing these recommendations, Justice, Energy, and Homeland Security should be in a better position to handle the risks associated with their chain of IT suppliers.
To learn more, read our full testimony.
Comments on GAO’s WatchBlog? Contact blog@gao.gov.
GAO Contacts
Related Products

GAO's mission is to provide Congress with fact-based, nonpartisan information that can help improve federal government performance and ensure accountability for the benefit of the American people. GAO launched its WatchBlog in January, 2014, as part of its continuing effort to reach its audiences—Congress and the American people—where they are currently looking for information.
The blog format allows GAO to provide a little more context about its work than it can offer on its other social media platforms. Posts will tie GAO work to current events and the news; show how GAO’s work is affecting agencies or legislation; highlight reports, testimonies, and issue areas where GAO does work; and provide information about GAO itself, among other things.
Please send any feedback on GAO's WatchBlog to blog@gao.gov.