Critical Infrastructure Protection: Actions Needed to Address Significant Cybersecurity Risks Facing the Electric Grid
Fast Facts
The nation’s electric grid is becoming more vulnerable to cyberattacks—particularly those involving industrial control systems that support grid operations. Recent federal assessments indicate that cyberattacks could cause widespread power outages in the United States, but the scale of such outages is uncertain.
The Department of Energy (DOE) plays a key role in helping address cybersecurity risks in each component of the electric grid’s infrastructure. However, DOE has not developed plans for electric grid cybersecurity that address the key characteristics needed for a national strategy.
We recommended that it do so.
An illustration of powerlines
An illustration of powerlines connected to a tower
Highlights
What GAO Found
The electric grid faces significant cybersecurity risks:
Threat actors. Nations, criminal groups, terrorists, and others are increasingly capable of attacking the grid.
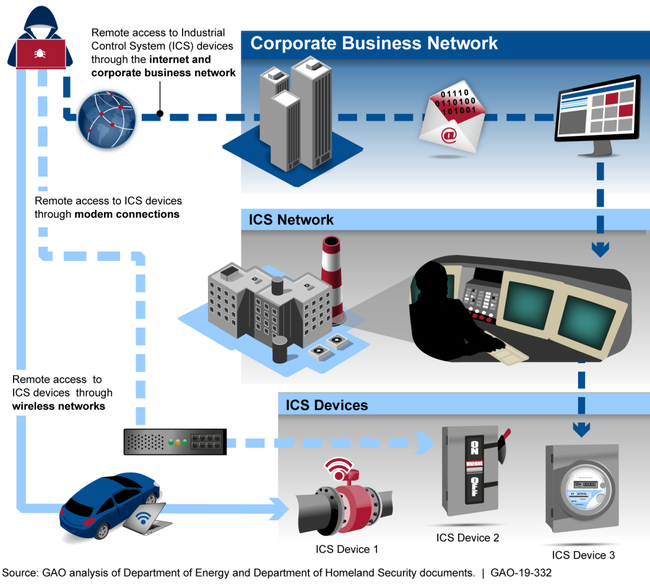
Vulnerabilities. The grid is becoming more vulnerable to cyberattacks—particularly those involving industrial control systems that support grid operations. (The figure below is a high-level depiction of ways in which an attacker could compromise industrial control systems.) The increasing adoption of high-wattage consumer Internet of Things devices—“smart” devices connected to the internet—and the use of the global positioning system to synchronize grid operations are also vulnerabilities.
Impacts. Although cybersecurity incidents reportedly have not resulted in power outages domestically, cyberattacks on industrial control systems have disrupted foreign electric grid operations. In addition, while recent federal assessments indicate that cyberattacks could cause widespread power outages in the United States, the scale of power outages that may result from a cyberattack is uncertain due to limitations in those assessments.
Potential Ways an Attacker Could Compromise Industrial Control System Devices
Although the Department of Energy (DOE) has developed plans and an assessment to implement a federal strategy for addressing grid cybersecurity risks, these documents do not fully address all of the key characteristics needed for a national strategy. For example, while DOE conducted a risk assessment, that assessment had significant methodological limitations and did not fully analyze grid cybersecurity risks. One such key limitation was that the assessment used a model that covered only a portion of the grid and reflected how that portion existed around 1980. Until DOE has a complete grid cybersecurity plan, the guidance the plan provides decision makers in allocating resources to address those risks will likely be limited.
The Federal Energy Regulatory Commission (FERC)—the regulator for the interstate transmission of electricity—has approved mandatory grid cybersecurity standards. However, it has not ensured that those standards fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework. (See table below for an excerpt of GAO's analysis of two of the five framework functions.) Without a full consideration of the framework, there is increased risk that grid entities will not fully implement leading cybersecurity practices.
Extent to Which FERC-Approved Cybersecurity Standards Address the National Institute of Standards and Technology Cybersecurity Framework's Identify and Protect Functions
|
Function |
GAO assessment |
Category |
GAO assessment |
|
Identify
|
◑
|
Asset management |
◑ |
|
Business environment |
○ |
||
|
Governance |
◑ |
||
|
Risk assessment |
◕ |
||
|
Risk management strategy |
○ |
||
|
Supply chain risk management |
◑ |
||
|
Protect
|
◕
|
Identity management, authentication, and access control |
● |
|
Awareness and training |
◑ |
||
|
Data security |
◑ |
||
|
Information protection processes and procedures |
◕ |
||
|
Maintenance |
◑ |
||
|
Protective technology |
◑ |
Legend: ●—Fully address. ◕—Substantially address. ◑—Partially address. ◔—Minimally address.○—Do not address .
Source: GAO analysis of Federal Energy Regulatory Commission (FERC)-approved cybersecurity standards. | GAO-19-332
In addition, FERC's approved threshold for which entities must comply with the requirements in the full set of grid cybersecurity standards is based on an analysis that did not evaluate the potential risk of a coordinated cyberattack on geographically distributed targets. Such an attack could target, for example, a combination of geographically dispersed systems that each fall below the threshold for complying with the full set of standards. Responding to such an attack could be more difficult than to a localized event since resources may be geographically distributed rather than concentrated in the same area. Without information on the risk of such an attack, FERC does not have assurance that its approved threshold for mandatory compliance adequately responds to that risk.
Why GAO Did This Study
The nation's electric grid—the commercial electric power generation, transmission, and distribution system comprising power lines and other infrastructure—delivers the electricity that is essential for modern life. As a result, the reliability of the grid—its ability to meet consumers' electricity demand at all times—has been of long-standing national interest.
GAO was asked to review the cybersecurity of the grid. Among other things, this report (1) describes the cybersecurity risks facing the grid, (2) assesses the extent to which DOE has defined a strategy for addressing grid cybersecurity risks, and (3) assesses the extent to which FERC-approved standards address grid cybersecurity risks.
To do so, GAO developed a list of cyber actors that could pose a threat to the grid; identified key vulnerable components and processes that could be exploited; and reviewed studies on the potential impact of cyberattacks on the grid by reviewing prior GAO and industry reports, as well as interviewing representatives from federal and nonfederal entities. GAO also analyzed DOE's approaches to implementing a federal cybersecurity strategy for the energy sector as it relates to the grid and assessed FERC oversight of cybersecurity standards for the grid.
Recommendations
GAO is making three recommendations—one to DOE and two to FERC.
GAO is making a recommendation to DOE to develop a plan aimed at implementing the federal cybersecurity strategy for the grid and ensure that the plan addresses the key characteristics of a national strategy, including a full assessment of cybersecurity risks to the grid.
GAO is also making the following two recommendations to FERC:
1. Consider adopting changes to its approved cybersecurity standards to more fully address the NIST Cybersecurity Framework.
2. Evaluate the potential risk of a coordinated cyberattack on geographically distributed targets and, based on the results of that evaluation, determine if changes are needed in the threshold for mandatory compliance with requirements in the full set of cybersecurity standards.
DOE and FERC agreed with GAO’s recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Energy |
Priority Rec.
The Secretary of Energy, in coordination with DHS and other relevant stakeholders, should develop a plan aimed at implementing the federal cybersecurity strategy for the electric grid and ensure that the plan addresses the key characteristics of a national strategy, including a full assessment of cybersecurity risks to the grid. (Recommendation 1) |
According to DOE officials, the department is (1) examining cybersecurity risks to the electricity grid as part of an overall risk characterization effort that will also consider other threats and hazards, and (2) evaluating combined physical-cyber attack scenarios to address GAO's recommendation. As of April 2024, DOE did not have an estimated date for issuing a plan related to addressing all of the key characteristics needed to implement a national strategy, such as fully assessing cybersecurity risks to the electricity grid. DOE needs to develop a plan for implementing the federal cybersecurity strategy for the electric grid, ensure that the plan addresses the key characteristics of a national strategy, and coordinate that plan with the Department of Homeland Security and other relevant stakeholders.
|
| Federal Energy Regulatory Commission | FERC should consider our assessment and determine whether to direct the North American Electric Reliability Corporation (NERC) to adopt any changes to its cybersecurity standards to ensure those standards more fully address the NIST Cybersecurity framework and address current and projected risks. (Recommendation 2) |
FERC agreed with our recommendation and has taken steps to partially address this recommendation. Specifically, in June 2020, FERC issued a Notice of Inquiry seeking comments on whether NERC's cybersecurity standards adequately address certain NIST Cybersecurity Framework categories. Although FERC officials told us that the agency completed its review of public comments on the Notice of Inquiry in June 2023, FERC has not provided the results of its assessment or any relevant changes to the cybersecurity standards based on this assessment. We will continue to monitor FERC's progress to implement our recommendation.
|
| Federal Energy Regulatory Commission | FERC should (1) evaluate the potential risk of a coordinated cyberattack on geographically distributed targets and, (2) based on the results of that evaluation, determine whether to direct NERC to make any changes to the threshold for mandatory compliance with requirements in the full set of cybersecurity standards. (Recommendation 3) |
FERC agreed with our recommendation and has taken steps to partially address this recommendation. Specifically, in June 2020, FERC issued a Notice of Inquiry seeking comments on whether modifications to the cybersecurity standards would be appropriate to address the potential risk of a coordinated cyberattack on geographically distributed targets. FERC officials told us that the agency completed its review of public comments on the Notice of Inquiry in June 2023. In addition, FERC officials also engaged with NERC on a project that identified the risk posed by an orchestrated coordinated cyberattack against multiple distributed targets that individually would generally be a localized event. The project resulted in an October 2022 whitepaper on low impact criteria that made a variety of recommendations including revising Critical Infrastructure Protection Reliability Standards, developing security guidelines, and continuous monitoring of access attempts. According to FERC officials, NERC is currently working to implement these recommendations and FERC officials remain actively engaged and will assess new or modified Reliability Standards when they are developed and filed by NERC. Further, the Commission issued Order No. 893, Incentives for Advanced Cybersecurity Investment. The Order revises FERC regulations for incentive-based rate treatments to encourage advanced cybersecurity technology and participation in cybersecurity threat information sharing programs in accordance with the Infrastructure Investment and Jobs Act of 2021. For example, for an entity to receive an incentive, the Commission will evaluate whether a voluntary investment in security controls satisfies an objective found in the NIST Cybersecurity Framework and protects against cybersecurity risks for cyber assets that are not currently protected by the Critical Infrastructure Protection Reliability Standards. Although FERC has evaluated the potential risk of a coordinated cyberattack on geographically distributed targets, it has not yet determined whether to direct NERC to make any changes to the threshold for mandatory compliance with requirements in the full set of cybersecurity standards. We will continue to monitor FERC's progress to implement our recommendation.
|
